Security/Automatic Private Browsing Upgrades: Difference between revisions
< Security
Jump to navigation
Jump to search
(Added toolbar indicator) |
(→Triggers: clean up the layout) |
||
| Line 26: | Line 26: | ||
== Triggers == | == Triggers == | ||
[[File:Automatic-private-browsing-upgrades-toolbar-indicator.png|300px|thumb|right|Notification bar]] | |||
There are three ways to trigger it: | There are three ways to trigger it: | ||
| Line 35: | Line 37: | ||
Once triggered, the following happens: | Once triggered, the following happens: | ||
# We open the "protected" URL in a new private browsing window | # We open the "protected" URL in a new private browsing window and show a notification bar | ||
# The original tab is navigated to <tt>about:blank</tt> (or maybe closed if it doesn't have any history) | # The original tab is navigated to <tt>about:blank</tt> (or maybe closed if it doesn't have any history) | ||
# We delete the protected URL from the history | # We delete the protected URL from the history | ||
| Line 42: | Line 43: | ||
[[File:Automatic-private-browsing-upgrades.gif]] | [[File:Automatic-private-browsing-upgrades.gif]] | ||
== Prospective clients == | == Prospective clients == | ||
Revision as of 06:05, 26 August 2015
Description
The goal of this feature is to provide a way for website authors to tell Firefox that the site should only be viewed while in Private Browsing.
A bit like HSTS but for local attackers.
Delivery Mechanism
We define a new require-private CSP directive. It can be delivered as an HTTP header:
Content-Security-Policy: require-private
or as a meta tag inside the page's head:
<head> <meta http-equiv="content-security-policy" content="require-private"> </head>
Note on fingerprinting
This is not meant as a way for a site to probe whether or not the user is in Private Browsing mode. It could be used for that, but using it would cause some pretty major UX disruptions.
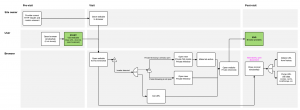
Triggers
There are three ways to trigger it:
- Typing a URL in the address bar and pressing Enter
- Opening a bookmark
- Clicking a link
Once triggered, the following happens:
- We open the "protected" URL in a new private browsing window and show a notification bar
- The original tab is navigated to about:blank (or maybe closed if it doesn't have any history)
- We delete the protected URL from the history
- We purge all site data (cookies, localStorage, cache, etc.) associated with the protected URL
Prospective clients
Example websites that might be interested:
- https://womensrefuge.org.nz/WR/Legal/Internet-Safety
- http://shakti-international.org/how-to-hide-my-visit/
- http://www.kidshelpphone.ca/Teens/AboutUs/How-to-Keep-it-Private.aspx
- http://www.childline.org.uk/explore/onlinesafety/pages/covertracks.aspx
Example websites without tutorial on hiding your tracks:
Related
- Initial idea (W3C Privacy Interest Group)
- Blushproof: detecting when private browsing should be used and prompting users
- Clear Site data: new spec to allow sites to clear site data themselves
- Upgrade insecure requests: another spec which defines a new CSP directive