PluginUpdating: Difference between revisions
No edit summary |
|||
| (51 intermediate revisions by 4 users not shown) | |||
| Line 3: | Line 3: | ||
= Proposal = | = Proposal = | ||
Create a service anybody can use on any site to increase plugin awareness for their users. | |||
== Components == | == Components == | ||
* | Tracker bug: {{bug|465898}} | ||
* | |||
* Create database to store plugin information {{bug|465888}} | |||
* Plugins service to serve plugin metadata via XML or JSON {{bug|465891}} | |||
* Create javascript library for embedding {{bug|465891}} | |||
mozilla.com areas of influence: | |||
* Firstrun page | |||
* What's new page | |||
* Upyourplug page | |||
= Landing pages = | = Landing pages = | ||
== First Run | == First Run == | ||
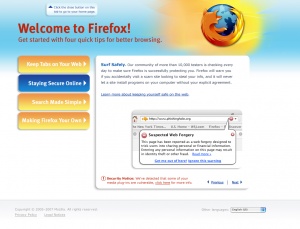
[[Image:FIRST RUN p2ALT MAC.jpg|thumb]] | |||
Add an alert that checks the first time a user opens Firefox: | Add an alert that checks the first time a user opens Firefox: | ||
'''Message:''' ''We detected that some of your media plug-ins are vulnerable, click here for more info.'' | '''Message:''' ''We detected that some of your media plug-ins are vulnerable, click here for more info.'' | ||
This | This is non-invasive, as we do not want to have the user have trouble getting started with Firefox. | ||
This will lead the user to the [[#UpYourPlug page|plug-in check page]]. | |||
'''comment''' [morgamic] -- please eliminate the "click here". A "more info" that is a hyperlink should be sufficient. "click here" is bad wording for a hyperlink because it's non-descriptive. When I was messing with it, "Update your plug-ins." seemed even better -- but just pick something besides "click here". :) | |||
'''comment''' [[User:Clouserw|clouserw]] -- "vulnerable" is a pretty strong word. Are we actually detecting that they are using versions that are vulnerable, or just that they are using outdated versions? | |||
'''comment ''' [[User:Polvi|polvi]] -- The goal is to detect vulnerable plug-ins, not outdated ones (although, they often go hand in hand). Regarding "click here", I agree, but we are trying to structure the language such that it avoids demanding something of the user. | |||
== Updated == | |||
Add similar alert to the "you've been updated" page which leads to the [[#UpYourPlug page|plug-in check page]]. | |||
== Implementation == | |||
It will be easiest to check the basic functionality in Javascript. [https://bugzilla.mozilla.org/show_bug.cgi?id=282257 Bug 282258] has a script that should work for flash and java. | |||
= UpYourPlug page = | |||
This page will do a check on common plug-ins and see if they are vulnerable or not. [http://www.guninski.com/mozbugs/plug-test.html An example implementation can be found here.] | |||
Plug-ins to check: | |||
* [http://java.com/en/download/installed.jsp?detect=jre&try=1 Java] (system update) | |||
* [http://www.adobe.com/shockwave/welcome/ Flash] (provides API, system update) | |||
Future plug-ins to check: | |||
* Windows media player (system update) | |||
* Real player (system update) | |||
* Quicktime (system update) | |||
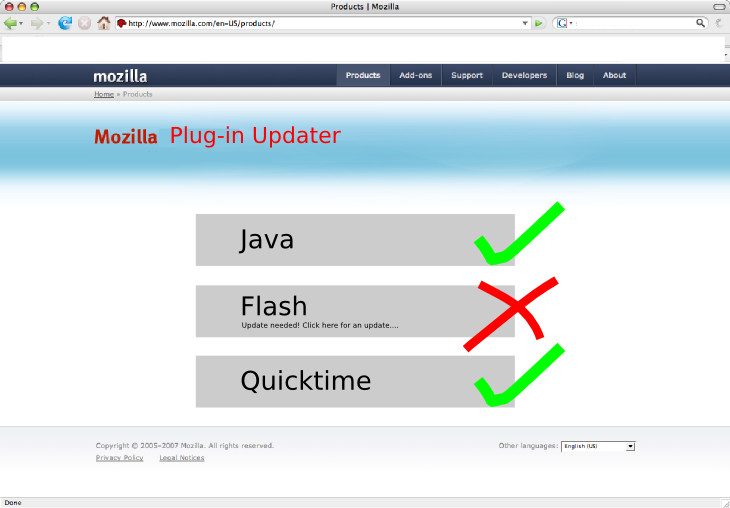
== Mock-up == | |||
Here is a cheesy mock-up of the idea for the plug-in update check page. | |||
[[Image:UpYourPlug.png]] | |||
== Implementation == | |||
The actual checks need to be implemented in javascript. The following use cases should be handled accordingly: | |||
* '''Plugin installed and up to date''': An green "OK" box displayed linked to vendor | |||
* '''Plugin installed and out of date''': A red "need update" box displayed linked to vendor | |||
* '''Plugin not installed''': A gray "not installed" box displayed. | |||
=== Java on the Mac === | |||
Since only the java embedding plugin gives version information to javascript, we cannot check for this case without a java applet. In this case, display a gray "check with vendor" box that links to Sun's java plugin page. | |||
=== Non-Firefox Browsers === | |||
If a non Firefox browser hits this page, we need to display a notice with the rest of the copy on the page: "This page is only supported when using Firefox". Then all the checks should be a gray "check with vendor" box that link accordingly. | |||
== Determining the latest secure version == | |||
Ideally we would talk to the upstream provider and get the latest secure version. However, initially we can just maintain a file that includes the latest versions of the plug-ins. | |||
== We found an insecure plug-in, now what? == | |||
After we detect that a plug-in is out of date, we should open the vendor page in a new tab. | |||
One major concern is that each plug-in update needs a browser restart. | |||
=== Java === | |||
[http://java.com/en/download/installed.jsp?detect=jre&try=1 Sun provides an update check]. Linking here should provide a sufficient starting point for getting java up to date. | |||
=== Flash === | |||
[http://www.adobe.com/shockwave/welcome/ Adobe provides an update check]. The user will be offered to navigate to this page for the update. | |||
= Schedule = | |||
A rough timeline... | |||
# First run revamp launch ~ August 24th | |||
# Finish UpYourPlug page ~ August 24th | |||
# Launch page and add detection to first run page - August 31th | |||
# Add detection to updated page - September 7th | |||
= QA Matrix = | |||
All platforms for Firefox < 2.0.0.7 | |||
{| class="fullwidth-table" | |||
! Flash version | |||
! Quicktime | |||
! Java | |||
! | |||
! firstrun notice | |||
! Flash | |||
! Quicktime | |||
! Java | |||
|- | |||
| >= 9.0r47 (win,mac) | |||
| >= 7.2.0 | |||
| >= 1.5.0_07 | |||
| | |||
| no | |||
| green | |||
| green | |||
| green | |||
|- | |||
| >= 9.0r48 (lin) | |||
| >= 7.2.0 | |||
| >= 1.5.0_07 | |||
| | |||
| no | |||
| green | |||
| green | |||
| green | |||
|- | |||
| < 9.0r47 (win,mac) | |||
| >= 7.2.0 | |||
| >= 1.5.0_07 | |||
| | |||
| yes | |||
| red | |||
| green | |||
| green | |||
|- | |||
| < 9.0r48 (lin) | |||
| >= 7.2.0 | |||
| >= 1.5.0_07 | |||
| | |||
| yes | |||
| red | |||
| green | |||
| green | |||
|- | |||
| >= 9.0r47 | |||
| < 7.2.0 | |||
| < 1.5.0_07 (all) | |||
| | |||
| yes | |||
| green | |||
| red | |||
| green | |||
|- | |||
| >= 9.0r47 | |||
| >= 7.2.0 | |||
| < 1.5.0_07 (all) | |||
| | |||
| yes | |||
| green | |||
| green | |||
| red | |||
|} | |||
= References = | |||
* [https://bugzilla.mozilla.org/show_bug.cgi?id=282257 bug + possible javascript] | |||
* [http://www.adobe.com/devnet/flashplayer/articles/fp8_security-related_apis.pdf Possible Flash API for determining an update] | |||
* [http://gemal.dk/browserspy/ Javascript library providing some plug-in detection functionality] | |||
* [http://www.adobe.com/shockwave/welcome/ Adobe's flash checker] | |||
* [https://bugzilla.mozilla.org/show_bug.cgi?id=391433 scripting work bug] | |||
= Postmortem = | |||
* be more specific about <strike>copy</strike> wording and mock-up layout | |||
* note when the alerts should display | |||
* s/sans/without/ | |||
* think of edge cases ahead of time if possible | |||
* talk about projects like this at start of quarters to get a better response | |||
Latest revision as of 18:30, 23 January 2009
Problem Statement
Our users often get hacked via vulnerable third party plug-ins.
Proposal
Create a service anybody can use on any site to increase plugin awareness for their users.
Components
Tracker bug: bug 465898
- Create database to store plugin information bug 465888
- Plugins service to serve plugin metadata via XML or JSON bug 465891
- Create javascript library for embedding bug 465891
mozilla.com areas of influence:
- Firstrun page
- What's new page
- Upyourplug page
Landing pages
First Run
Add an alert that checks the first time a user opens Firefox:
Message: We detected that some of your media plug-ins are vulnerable, click here for more info.
This is non-invasive, as we do not want to have the user have trouble getting started with Firefox.
This will lead the user to the plug-in check page.
comment [morgamic] -- please eliminate the "click here". A "more info" that is a hyperlink should be sufficient. "click here" is bad wording for a hyperlink because it's non-descriptive. When I was messing with it, "Update your plug-ins." seemed even better -- but just pick something besides "click here". :)
comment clouserw -- "vulnerable" is a pretty strong word. Are we actually detecting that they are using versions that are vulnerable, or just that they are using outdated versions?
comment polvi -- The goal is to detect vulnerable plug-ins, not outdated ones (although, they often go hand in hand). Regarding "click here", I agree, but we are trying to structure the language such that it avoids demanding something of the user.
Updated
Add similar alert to the "you've been updated" page which leads to the plug-in check page.
Implementation
It will be easiest to check the basic functionality in Javascript. Bug 282258 has a script that should work for flash and java.
UpYourPlug page
This page will do a check on common plug-ins and see if they are vulnerable or not. An example implementation can be found here.
Plug-ins to check:
Future plug-ins to check:
- Windows media player (system update)
- Real player (system update)
- Quicktime (system update)
Mock-up
Here is a cheesy mock-up of the idea for the plug-in update check page.
Implementation
The actual checks need to be implemented in javascript. The following use cases should be handled accordingly:
- Plugin installed and up to date: An green "OK" box displayed linked to vendor
- Plugin installed and out of date: A red "need update" box displayed linked to vendor
- Plugin not installed: A gray "not installed" box displayed.
Java on the Mac
Since only the java embedding plugin gives version information to javascript, we cannot check for this case without a java applet. In this case, display a gray "check with vendor" box that links to Sun's java plugin page.
Non-Firefox Browsers
If a non Firefox browser hits this page, we need to display a notice with the rest of the copy on the page: "This page is only supported when using Firefox". Then all the checks should be a gray "check with vendor" box that link accordingly.
Determining the latest secure version
Ideally we would talk to the upstream provider and get the latest secure version. However, initially we can just maintain a file that includes the latest versions of the plug-ins.
We found an insecure plug-in, now what?
After we detect that a plug-in is out of date, we should open the vendor page in a new tab.
One major concern is that each plug-in update needs a browser restart.
Java
Sun provides an update check. Linking here should provide a sufficient starting point for getting java up to date.
Flash
Adobe provides an update check. The user will be offered to navigate to this page for the update.
Schedule
A rough timeline...
- First run revamp launch ~ August 24th
- Finish UpYourPlug page ~ August 24th
- Launch page and add detection to first run page - August 31th
- Add detection to updated page - September 7th
QA Matrix
All platforms for Firefox < 2.0.0.7
| Flash version | Quicktime | Java | firstrun notice | Flash | Quicktime | Java | |
|---|---|---|---|---|---|---|---|
| >= 9.0r47 (win,mac) | >= 7.2.0 | >= 1.5.0_07 | no | green | green | green | |
| >= 9.0r48 (lin) | >= 7.2.0 | >= 1.5.0_07 | no | green | green | green | |
| < 9.0r47 (win,mac) | >= 7.2.0 | >= 1.5.0_07 | yes | red | green | green | |
| < 9.0r48 (lin) | >= 7.2.0 | >= 1.5.0_07 | yes | red | green | green | |
| >= 9.0r47 | < 7.2.0 | < 1.5.0_07 (all) | yes | green | red | green | |
| >= 9.0r47 | >= 7.2.0 | < 1.5.0_07 (all) | yes | green | green | red |
References
- bug + possible javascript
- Possible Flash API for determining an update
- Javascript library providing some plug-in detection functionality
- Adobe's flash checker
- scripting work bug
Postmortem
- be more specific about
copywording and mock-up layout - note when the alerts should display
- s/sans/without/
- think of edge cases ahead of time if possible
- talk about projects like this at start of quarters to get a better response