Security/Server Side TLS: Difference between revisions
(Fix a few typos) |
(Update to commit 7a81eec5519983e1408cafe4936b4f85ae6a0997) |
||
| (174 intermediate revisions by 17 users not shown) | |||
| Line 1: | Line 1: | ||
The goal of this document is to help operational teams with the configuration of TLS | <table> | ||
<tr> | |||
<td style="min-width: 25em;">__TOC__</td> | |||
<td style="vertical-align: top; max-width: 60em; padding-left: .75rem;">The goal of this document is to help operational teams with the configuration of TLS. All Mozilla websites and deployments should follow the recommendations below. | |||
Mozilla maintains this document as a reference guide for navigating the TLS landscape, as well as a [https://ssl-config.mozilla.org configuration generator] to assist system administrators. Changes are reviewed and merged by the Mozilla Operations Security and Enterprise Information Security teams. | |||
Updates to this page should be submitted to the [https://github.com/mozilla/server-side-tls server-side-tls] repository on GitHub. Issues related to the [https://ssl-config.mozilla.org configuration generator] are maintained in their own [https://github.com/mozilla/ssl-config-generator GitHub repository]. | |||
In the interests of usability and maintainability, these guidelines have been considerably simplified from the [[Security/Archive/Server Side TLS 4.0|previous guidelines]]. | |||
</td> | |||
</tr> | |||
</table> | |||
The | = Recommended configurations = | ||
<span style="float: right; max-width: 600px; text-align: center;"> | |||
[[Image:Ssl-config.mozilla.org.png|600px|link=https://ssl-config.mozilla.org/|Mozilla SSL Configuration Generator]]<br> | |||
The [https://ssl-config.mozilla.org/ Mozilla SSL Configuration Generator] | |||
</span> | |||
Mozilla maintains three recommended configurations for servers using TLS. Pick the correct configuration depending on your audience: | |||
''' | * <span style="color: green; font-weight: bold;">Modern</span>''':''' Modern clients that support TLS 1.3, with no need for backwards compatibility | ||
* <span style="color: orange; font-weight: bold;">Intermediate</span>''':''' Recommended configuration for a general-purpose server | |||
* <span style="color: gray; font-weight: bold;">Old</span>''':''' Services accessed by very old clients or libraries, such as Internet Explorer 8 (Windows XP), Java 6, or OpenSSL 0.9.8 | |||
{| class="wikitable" style="margin: 1.5rem 1rem;" | |||
|- | |||
! Configuration | |||
! Firefox | |||
! Android | |||
! Chrome | |||
! Edge | |||
! Internet Explorer | |||
! Java | |||
! OpenSSL | |||
! Opera | |||
! Safari | |||
|- | |||
| style="color: green;" | '''Modern''' | |||
| style="text-align: center;" | 63 | |||
| style="text-align: center;" | 10.0 | |||
| style="text-align: center;" | 70 | |||
| style="text-align: center;" | 75 | |||
| style="text-align: center;" | -- | |||
| style="text-align: center;" | 11 | |||
| style="text-align: center;" | 1.1.1 | |||
| style="text-align: center;" | 57 | |||
| style="text-align: center;" | 12.1 | |||
|- | |||
| style="color:orange;" | '''Intermediate''' | |||
| style="text-align: center;" | 27 | |||
| style="text-align: center;" | 4.4.2 | |||
| style="text-align: center;" | 31 | |||
| style="text-align: center;" | 12 | |||
| style="text-align: center;" | 11 (Win7) | |||
| style="text-align: center;" | 8u31 | |||
| style="text-align: center;" | 1.0.1 | |||
| style="text-align: center;" | 20 | |||
| style="text-align: center;" | 9 | |||
|- | |||
| style="color:gray;" | '''Old''' | |||
| style="text-align: center;" | 1 | |||
| style="text-align: center;" | 2.3 | |||
| style="text-align: center;" | 1 | |||
| style="text-align: center;" | 12 | |||
| style="text-align: center;" | 8 (WinXP) | |||
| style="text-align: center;" | 6 | |||
| style="text-align: center;" | 0.9.8 | |||
| style="text-align: center;" | 5 | |||
| style="text-align: center;" | 1 | |||
|} | |||
= | <p style="max-width: 60em;">The ordering of cipher suites in the <span style="color: gray; font-weight: bold;">Old</span> configuration is very important, as it determines the priority with which algorithms are selected.</p> | ||
<p style="max-width: 60em;">OpenSSL will ignore cipher suites it doesn't understand, so always use the full set of cipher suites below, in their recommended order. The use of the <span style="color: gray; font-weight: bold;">Old</span> configuration with modern versions of OpenSSL may require custom builds with support for deprecated ciphers.</p> | |||
<br style="clear: right;"> | |||
== <span style="color:green;">'''Modern'''</span> compatibility == | |||
For services with clients that support TLS 1.3 and don't need backward compatibility, the <span style="color: green; font-weight: bold;">Modern</span> configuration provides an extremely high level of security. | |||
* Cipher suites (TLS 1.3): '''TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256''' | |||
* Cipher suites (TLS 1.2): (none) | |||
* Protocols: '''TLS 1.3''' | |||
* Certificate type: '''ECDSA (P-256)''' | |||
* TLS curves: '''X25519, prime256v1, secp384r1''' | |||
* HSTS: '''max-age=63072000''' (two years) | |||
* Certificate lifespan: '''90 days''' | |||
* Cipher preference: '''client chooses''' | |||
<!-- This tabular openssl list can be produced by running "openssl ciphers -V" --> | |||
<source> | |||
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD | |||
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD | |||
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
</source> | </source> | ||
* Rationale: | |||
** All cipher suites are [https://en.wikipedia.org/wiki/Forward_secrecy forward secret] and [https://en.wikipedia.org/wiki/Authenticated_encryption authenticated] | |||
** The cipher suites are all strong and so we allow the client to choose, as they will know best if they have support for hardware-accelerated AES | |||
** We recommend ECDSA certificates using P-256, as P-384 provides negligible improvements to security and Ed25519 is not yet widely supported | |||
The | |||
== <span style="color:orange;">'''Intermediate'''</span> compatibility (recommended) == | |||
<p style="max-width: 60em;">For services that don't need compatibility with legacy clients such as Windows XP or old versions of OpenSSL. This is the recommended configuration for the vast majority of services, as it is highly secure and compatible with nearly every client released in the last five (or more) years.</p> | |||
</ | |||
= | * Cipher suites (TLS 1.3): '''TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256''' | ||
* Cipher suites (TLS 1.2): '''ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305''' | |||
* Protocols: '''TLS 1.2, TLS 1.3''' | |||
* TLS curves: '''X25519, prime256v1, secp384r1''' | |||
* Certificate type: '''ECDSA (P-256)''' (recommended), or '''RSA (2048 bits)''' | |||
* DH parameter size: '''2048''' (ffdhe2048, [https://tools.ietf.org/html/rfc7919#appendix-A.1 RFC 7919]) | |||
* HSTS: '''max-age=63072000''' (two years) | |||
* Certificate lifespan: '''90 days''' (recommended) to '''366 days''' | |||
* Cipher preference: '''client chooses''' | |||
<!-- This tabular openssl list can be produced by running "openssl ciphers -V" --> | |||
<source> | |||
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD | |||
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD | |||
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
0xC0,0x2B - ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD | |||
0xC0,0x2F - ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD | |||
0xC0,0x2C - ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD | |||
0xC0,0x30 - ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD | |||
0xCC,0xA9 - ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
== | 0xCC,0xA8 - ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | ||
0x00,0x9E - DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD | |||
0x00,0x9F - DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD | |||
0xCC,0xAA - DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
</source> | </source> | ||
* Rationale: | |||
** All cipher suites are [https://en.wikipedia.org/wiki/Forward_secrecy forward secret] and [https://en.wikipedia.org/wiki/Authenticated_encryption authenticated] | |||
** TLS 1.2 is the minimum supported protocol, as recommended by [https://tools.ietf.org/html/rfc7525#section-3.1.1 RFC 7525], PCI DSS, and others | |||
** ECDSA certificates are recommended over RSA certificates, as they allow the use of ECDHE with Windows 7 clients using Internet Explorer 11, as well as allow connections from IE11 on Windows Server 2008 R2 | |||
** The cipher suites are all strong and so we allow the client to choose, as they will know best if they have support for hardware-accelerated AES | |||
** Windows XP (including all embedded versions) are no longer supported by Microsoft, eliminating the need for many older protocols and ciphers | |||
</ | ** Administrators needing to provide access to [https://www.ssllabs.com/ssltest/viewClient.html?name=IE&version=11&platform=Win%207&key=36 IE 11 on Windows Server 2008 R2] and who are unable to switch to or add ECDSA certificates can add <tt>TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA</tt> | ||
** While the goal is to support a broad range of clients, we reasonably disable a number of ciphers that have little support (such as ARIA, Camellia, 3DES, and SEED) | |||
** 90 days is the recommended maximum certificate lifespan, to encourage certificate issuance automation | |||
< | == <span style="color:gray;">'''Old'''</span> backward compatibility == | ||
</ | |||
This configuration is compatible with a number of very old clients, and should be used only as a last resort. | |||
* Cipher suites (TLS 1.3): '''TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256''' | |||
* Cipher suites (TLS 1.0 - 1.2): '''ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA256:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA''' | |||
* Protocols: '''TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3''' | |||
* TLS curves: '''X25519, prime256v1, secp384r1''' | |||
* Certificate type: '''RSA (2048-bits)''' | |||
* Certificate curve: '''None''' | |||
* DH parameter size: '''1024''' (generated with <tt>openssl dhparam 1024</tt>) | |||
* HSTS: '''max-age=63072000''' (two years) | |||
* Certificate lifespan: '''90 days''' (recommended) to '''366 days''' | |||
* Cipher preference: '''server chooses''' | |||
<!-- This tabular openssl list can be produced by running "openssl ciphers -V" --> | |||
<source> | |||
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD | |||
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD | |||
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
0xC0,0x2B - ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD | |||
0xC0,0x2F - ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD | |||
0xC0,0x2C - ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD | |||
0xC0,0x30 - ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD | |||
0xCC,0xA9 - ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
0xCC,0xA8 - ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
0x00,0x9E - DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD | |||
0x00,0x9F - DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD | |||
0xCC,0xAA - DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD | |||
0xC0,0x23 - ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256 | |||
0xC0,0x27 - ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256 | |||
0xC0,0x09 - ECDHE-ECDSA-AES128-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1 | |||
0xC0,0x13 - ECDHE-RSA-AES128-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1 | |||
0xC0,0x24 - ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384 | |||
0xC0,0x28 - ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384 | |||
0xC0,0x0A - ECDHE-ECDSA-AES256-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1 | |||
0xC0,0x14 - ECDHE-RSA-AES256-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1 | |||
0x00,0x67 - DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256 | |||
0x00,0x6B - DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256 | |||
0x00,0x9C - AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD | |||
0x00,0x9D - AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD | |||
0x00,0x3C - AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256 | |||
0x00,0x3D - AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256 | |||
0x00,0x2F - AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1 | |||
0x00,0x35 - AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1 | |||
0x00,0x0A - DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1 | |||
</source> | </source> | ||
* Rationale: | |||
** Take a hard look at your infrastructure needs before using this configuration; it is intended for special use cases only | |||
** If possible, use this configuration only for endpoints that require it, segregating it from other traffic | |||
** SSLv3 has been disabled entirely, ending support for older Windows XP SP2 clients. Users requiring support for Windows XP SP2 may use [[Security/Archive/Server Side TLS 4.0|previous versions]] of this configuration, with the caveat that SSLv3 is no longer safe to use | |||
** This configuration requires custom builds to work with modern versions of OpenSSL, using <tt>enable-ssl3</tt>, <tt>enable-ssl3-method</tt>, <tt>enable-deprecated</tt>, and <tt>enable-weak-ssl-ciphers</tt> | |||
** Most ciphers that are not clearly broken and dangerous to use are supported | |||
= JSON version of the recommendations = | |||
<p style="max-width: 60em;">Mozilla also maintains [https://ssl-config.mozilla.org/guidelines/5.7.json these recommendations] in JSON format, for automated system configuration. This location is versioned and permanent, and can be referenced in scripts and tools. The file will not change, to avoid breaking tools when we update the recommendations.</p> | |||
= | <p style="max-width: 60em;">We also maintain a [https://ssl-config.mozilla.org/guidelines/latest.json rolling version] of these recommendations, with the caveat that they may change '''without warning''' and '''without providing backwards compatibility'''. As it may break things if you use it to automatically configure your servers without review, we recommend you use the [https://ssl-config.mozilla.org/guidelines/5.7.json version-specific file] instead.</p> | ||
= Version History = | |||
{| class="wikitable" | {| class="wikitable" | ||
|- | |- | ||
| | ! Version | ||
! Editor | |||
! Changes | |||
|- | |||
| style="text-align: center;" | 5.7 | |||
| style="text-align: center;" | Gene Wood | |||
| Add DHE-RSA-CHACHA20-POLY1305 cipher to the Intermediate configuration | |||
|- | |||
| style="text-align: center;" | 5.6 | |||
| style="text-align: center;" | April King | |||
| Fixed incorrect cipher ordering for the Intermediate configuration | |||
|- | |||
| style="text-align: center;" | 5.5 | |||
| style="text-align: center;" | April King | |||
| Update certificate lifespan to reflect browser policy changes | |||
|- | |||
| style="text-align: center;" | 5.3 | |||
| style="text-align: center;" | April King | |||
| Bump links to point to 5.3 guidelines, since it fixes a small JSON error | |||
|- | |||
| style="text-align: center;" | 5.0.1 | |||
| style="text-align: center;" | April King | |||
| Add note about IE 11 on Windows Server 2008 R2 | |||
|- | |||
| style="text-align: center;" | 5.0 | |||
| style="text-align: center;" | April King | |||
| Server Side TLS 5.0 | |||
|- | |||
| style="text-align: center;" | 4.2 | |||
| style="text-align: center;" | April King | |||
| Updated cipher suite table | |||
|- | |- | ||
| | | style="text-align: center;" | 4.1 | ||
| style="text-align: center;" | Julien Vehent | |||
| Clarify Logjam notes, Clarify risk of TLS Tickets | |||
|- | |- | ||
| | | style="text-align: center;" | 4 | ||
| style="text-align: center;" | Julien Vehent | |||
| Recommend ECDSA in modern level, remove DSS ciphers, publish configurations as JSON | |||
|- | |- | ||
| | | style="text-align: center;" | 3.8 | ||
| | | style="text-align: center;" | Julien Vehent | ||
| redo cipher names chart (April King), move version chart (April King), update Intermediate cipher suite (ulfr) | |||
|- | |||
| style="text-align: center;" | 3.7 | |||
| style="text-align: center;" | Julien Vehent | |||
| cleanup version table (April King), add F5 conf samples (warburtron), add notes about DHE (rgacogne) | |||
|- | |||
| style="text-align: center;" | 3.6 | |||
| style="text-align: center;" | Julien Vehent | |||
| bump intermediate DHE to 2048, add note about java compatibility | |||
|- | |||
| style="text-align: center;" | 3.5 | |||
| style="text-align: center;" | alm | |||
| comment on weakdh vulnerability | |||
|- | |||
| style="text-align: center;" | 3.4 | |||
| style="text-align: center;" | Julien Vehent | |||
| added note about session resumption, HSTS, and HPKP | |||
|- | |||
| style="text-align: center;" | 3.3 | |||
| style="text-align: center;" | Julien Vehent | |||
| fix SHA256 prio, add POODLE details, update various templates | |||
|- | |||
| style="text-align: center;" | 3.2 | |||
| style="text-align: center;" | Julien Vehent | |||
| Added intermediate compatibility mode, renamed other modes | |||
|- | |||
| style="text-align: center;" | 3.1 | |||
| style="text-align: center;" | Julien Vehent | |||
| Added non-backward compatible ciphersuite | |||
|- | |||
| style="text-align: center;" | 3 | |||
| style="text-align: center;" | Julien Vehent | |||
| Remove RC4 for 3DES, fix ordering in openssl 0.9.8 ([https://bugzilla.mozilla.org/show_bug.cgi?id=1024430 1024430]), various minor updates | |||
|- | |||
| style="text-align: center;" | 2.5.1 | |||
| style="text-align: center;" | Julien Vehent | |||
| Revisit ELB capabilities | |||
|- | |||
| style="text-align: center;" | 2.5 | |||
| style="text-align: center;" | Julien Vehent | |||
| Update ZLB information for OCSP Stapling and ciphersuite | |||
|- | |||
| style="text-align: center;" | 2.4 | |||
| style="text-align: center;" | Julien Vehent | |||
| Moved a couple of aes128 above aes256 in the ciphersuite | |||
|- | |||
| style="text-align: center;" | 2.3 | |||
| style="text-align: center;" | Julien Vehent | |||
| Precisions on IE 7/8 AES support (thanks to Dobin Rutishauser) | |||
|- | |||
| style="text-align: center;" | 2.2 | |||
| style="text-align: center;" | Julien Vehent | |||
| Added IANA/OpenSSL/GnuTLS correspondence table and conversion tool | |||
|- | |||
| style="text-align: center;" | 2.1 | |||
| style="text-align: center;" | Julien Vehent | |||
| RC4 vs 3DES discussion. r=joes r=tinfoil | |||
|- | |||
| style="text-align: center;" | 2.0 | |||
| style="text-align: center;" | Julien Vehent, kang | |||
| Public release. | |||
|- | |||
| style="text-align: center;" | 1.5 | |||
| style="text-align: center;" | Julien Vehent, kang | |||
| added details for PFS DHE handshake, added nginx configuration details; added Apache recommended conf | |||
|- | |- | ||
| style="text-align: center;" | 1.4 | |||
|- | | style="text-align: center;" | Julien Vehent | ||
| | | revised ciphersuite. Prefer AES before RC4. Prefer 128 before 256. Prefer DHE before non-DHE. | ||
|- | |- | ||
| | | style="text-align: center;" | 1.3 | ||
| style="text-align: center;" | Julien Vehent | |||
| added netscaler example conf | |||
|- | |- | ||
| | | style="text-align: center;" | 1.2 | ||
| style="text-align: center;" | Julien Vehent | |||
| ciphersuite update, bump DHE-AESGCM above ECDH-RC4 | |||
|- | |- | ||
| | | style="text-align: center;" | 1.1 | ||
| style="text-align: center;" | Julien Vehent, kang | |||
| integrated review comments from Infra; SPDY information | |||
|- | |- | ||
| | | style="text-align: center;" | 1.0 | ||
| style="text-align: center;" | Julien Vehent | |||
| creation | |||
|- | |- | ||
| | | colspan="3" | | ||
|- | |- | ||
| | | colspan="2" style="border-right: none;" | '''Document Status:''' | ||
| style="border-left: none; color:green; text-align: center;" | '''READY''' | |||
|} | |} | ||
Latest revision as of 22:47, 16 May 2023
| The goal of this document is to help operational teams with the configuration of TLS. All Mozilla websites and deployments should follow the recommendations below.
Mozilla maintains this document as a reference guide for navigating the TLS landscape, as well as a configuration generator to assist system administrators. Changes are reviewed and merged by the Mozilla Operations Security and Enterprise Information Security teams. Updates to this page should be submitted to the server-side-tls repository on GitHub. Issues related to the configuration generator are maintained in their own GitHub repository. In the interests of usability and maintainability, these guidelines have been considerably simplified from the previous guidelines. |
Recommended configurations
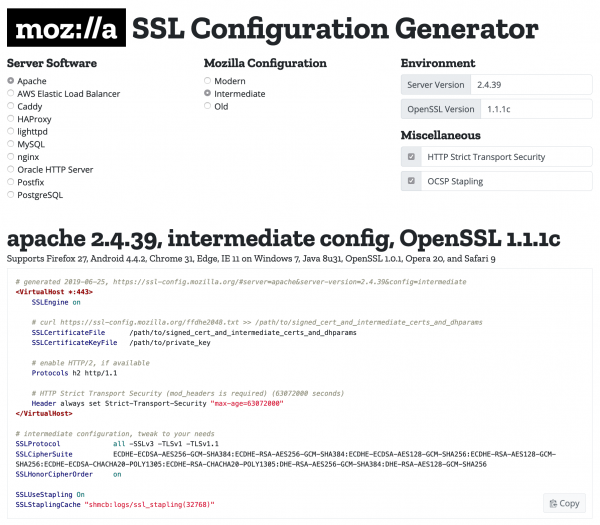
The Mozilla SSL Configuration Generator
Mozilla maintains three recommended configurations for servers using TLS. Pick the correct configuration depending on your audience:
- Modern: Modern clients that support TLS 1.3, with no need for backwards compatibility
- Intermediate: Recommended configuration for a general-purpose server
- Old: Services accessed by very old clients or libraries, such as Internet Explorer 8 (Windows XP), Java 6, or OpenSSL 0.9.8
| Configuration | Firefox | Android | Chrome | Edge | Internet Explorer | Java | OpenSSL | Opera | Safari |
|---|---|---|---|---|---|---|---|---|---|
| Modern | 63 | 10.0 | 70 | 75 | -- | 11 | 1.1.1 | 57 | 12.1 |
| Intermediate | 27 | 4.4.2 | 31 | 12 | 11 (Win7) | 8u31 | 1.0.1 | 20 | 9 |
| Old | 1 | 2.3 | 1 | 12 | 8 (WinXP) | 6 | 0.9.8 | 5 | 1 |
The ordering of cipher suites in the Old configuration is very important, as it determines the priority with which algorithms are selected.
OpenSSL will ignore cipher suites it doesn't understand, so always use the full set of cipher suites below, in their recommended order. The use of the Old configuration with modern versions of OpenSSL may require custom builds with support for deprecated ciphers.
Modern compatibility
For services with clients that support TLS 1.3 and don't need backward compatibility, the Modern configuration provides an extremely high level of security.
- Cipher suites (TLS 1.3): TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
- Cipher suites (TLS 1.2): (none)
- Protocols: TLS 1.3
- Certificate type: ECDSA (P-256)
- TLS curves: X25519, prime256v1, secp384r1
- HSTS: max-age=63072000 (two years)
- Certificate lifespan: 90 days
- Cipher preference: client chooses
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD- Rationale:
- All cipher suites are forward secret and authenticated
- The cipher suites are all strong and so we allow the client to choose, as they will know best if they have support for hardware-accelerated AES
- We recommend ECDSA certificates using P-256, as P-384 provides negligible improvements to security and Ed25519 is not yet widely supported
Intermediate compatibility (recommended)
For services that don't need compatibility with legacy clients such as Windows XP or old versions of OpenSSL. This is the recommended configuration for the vast majority of services, as it is highly secure and compatible with nearly every client released in the last five (or more) years.
- Cipher suites (TLS 1.3): TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
- Cipher suites (TLS 1.2): ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305
- Protocols: TLS 1.2, TLS 1.3
- TLS curves: X25519, prime256v1, secp384r1
- Certificate type: ECDSA (P-256) (recommended), or RSA (2048 bits)
- DH parameter size: 2048 (ffdhe2048, RFC 7919)
- HSTS: max-age=63072000 (two years)
- Certificate lifespan: 90 days (recommended) to 366 days
- Cipher preference: client chooses
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD
0xC0,0x2B - ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD
0xC0,0x2F - ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD
0xC0,0x2C - ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD
0xC0,0x30 - ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD
0xCC,0xA9 - ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
0xCC,0xA8 - ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
0x00,0x9E - DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD
0x00,0x9F - DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD
0xCC,0xAA - DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD- Rationale:
- All cipher suites are forward secret and authenticated
- TLS 1.2 is the minimum supported protocol, as recommended by RFC 7525, PCI DSS, and others
- ECDSA certificates are recommended over RSA certificates, as they allow the use of ECDHE with Windows 7 clients using Internet Explorer 11, as well as allow connections from IE11 on Windows Server 2008 R2
- The cipher suites are all strong and so we allow the client to choose, as they will know best if they have support for hardware-accelerated AES
- Windows XP (including all embedded versions) are no longer supported by Microsoft, eliminating the need for many older protocols and ciphers
- Administrators needing to provide access to IE 11 on Windows Server 2008 R2 and who are unable to switch to or add ECDSA certificates can add TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- While the goal is to support a broad range of clients, we reasonably disable a number of ciphers that have little support (such as ARIA, Camellia, 3DES, and SEED)
- 90 days is the recommended maximum certificate lifespan, to encourage certificate issuance automation
Old backward compatibility
This configuration is compatible with a number of very old clients, and should be used only as a last resort.
- Cipher suites (TLS 1.3): TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
- Cipher suites (TLS 1.0 - 1.2): ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA256:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA
- Protocols: TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3
- TLS curves: X25519, prime256v1, secp384r1
- Certificate type: RSA (2048-bits)
- Certificate curve: None
- DH parameter size: 1024 (generated with openssl dhparam 1024)
- HSTS: max-age=63072000 (two years)
- Certificate lifespan: 90 days (recommended) to 366 days
- Cipher preference: server chooses
0x13,0x01 - TLS_AES_128_GCM_SHA256 TLSv1.3 Kx=any Au=any Enc=AESGCM(128) Mac=AEAD
0x13,0x02 - TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD
0x13,0x03 - TLS_CHACHA20_POLY1305_SHA256 TLSv1.3 Kx=any Au=any Enc=CHACHA20/POLY1305(256) Mac=AEAD
0xC0,0x2B - ECDHE-ECDSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(128) Mac=AEAD
0xC0,0x2F - ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(128) Mac=AEAD
0xC0,0x2C - ECDHE-ECDSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AESGCM(256) Mac=AEAD
0xC0,0x30 - ECDHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AESGCM(256) Mac=AEAD
0xCC,0xA9 - ECDHE-ECDSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=ECDSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
0xCC,0xA8 - ECDHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=ECDH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
0x00,0x9E - DHE-RSA-AES128-GCM-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(128) Mac=AEAD
0x00,0x9F - DHE-RSA-AES256-GCM-SHA384 TLSv1.2 Kx=DH Au=RSA Enc=AESGCM(256) Mac=AEAD
0xCC,0xAA - DHE-RSA-CHACHA20-POLY1305 TLSv1.2 Kx=DH Au=RSA Enc=CHACHA20/POLY1305(256) Mac=AEAD
0xC0,0x23 - ECDHE-ECDSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA256
0xC0,0x27 - ECDHE-RSA-AES128-SHA256 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA256
0xC0,0x09 - ECDHE-ECDSA-AES128-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(128) Mac=SHA1
0xC0,0x13 - ECDHE-RSA-AES128-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(128) Mac=SHA1
0xC0,0x24 - ECDHE-ECDSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA384
0xC0,0x28 - ECDHE-RSA-AES256-SHA384 TLSv1.2 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA384
0xC0,0x0A - ECDHE-ECDSA-AES256-SHA TLSv1 Kx=ECDH Au=ECDSA Enc=AES(256) Mac=SHA1
0xC0,0x14 - ECDHE-RSA-AES256-SHA TLSv1 Kx=ECDH Au=RSA Enc=AES(256) Mac=SHA1
0x00,0x67 - DHE-RSA-AES128-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(128) Mac=SHA256
0x00,0x6B - DHE-RSA-AES256-SHA256 TLSv1.2 Kx=DH Au=RSA Enc=AES(256) Mac=SHA256
0x00,0x9C - AES128-GCM-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(128) Mac=AEAD
0x00,0x9D - AES256-GCM-SHA384 TLSv1.2 Kx=RSA Au=RSA Enc=AESGCM(256) Mac=AEAD
0x00,0x3C - AES128-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA256
0x00,0x3D - AES256-SHA256 TLSv1.2 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA256
0x00,0x2F - AES128-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(128) Mac=SHA1
0x00,0x35 - AES256-SHA SSLv3 Kx=RSA Au=RSA Enc=AES(256) Mac=SHA1
0x00,0x0A - DES-CBC3-SHA SSLv3 Kx=RSA Au=RSA Enc=3DES(168) Mac=SHA1- Rationale:
- Take a hard look at your infrastructure needs before using this configuration; it is intended for special use cases only
- If possible, use this configuration only for endpoints that require it, segregating it from other traffic
- SSLv3 has been disabled entirely, ending support for older Windows XP SP2 clients. Users requiring support for Windows XP SP2 may use previous versions of this configuration, with the caveat that SSLv3 is no longer safe to use
- This configuration requires custom builds to work with modern versions of OpenSSL, using enable-ssl3, enable-ssl3-method, enable-deprecated, and enable-weak-ssl-ciphers
- Most ciphers that are not clearly broken and dangerous to use are supported
JSON version of the recommendations
Mozilla also maintains these recommendations in JSON format, for automated system configuration. This location is versioned and permanent, and can be referenced in scripts and tools. The file will not change, to avoid breaking tools when we update the recommendations.
We also maintain a rolling version of these recommendations, with the caveat that they may change without warning and without providing backwards compatibility. As it may break things if you use it to automatically configure your servers without review, we recommend you use the version-specific file instead.
Version History
| Version | Editor | Changes |
|---|---|---|
| 5.7 | Gene Wood | Add DHE-RSA-CHACHA20-POLY1305 cipher to the Intermediate configuration |
| 5.6 | April King | Fixed incorrect cipher ordering for the Intermediate configuration |
| 5.5 | April King | Update certificate lifespan to reflect browser policy changes |
| 5.3 | April King | Bump links to point to 5.3 guidelines, since it fixes a small JSON error |
| 5.0.1 | April King | Add note about IE 11 on Windows Server 2008 R2 |
| 5.0 | April King | Server Side TLS 5.0 |
| 4.2 | April King | Updated cipher suite table |
| 4.1 | Julien Vehent | Clarify Logjam notes, Clarify risk of TLS Tickets |
| 4 | Julien Vehent | Recommend ECDSA in modern level, remove DSS ciphers, publish configurations as JSON |
| 3.8 | Julien Vehent | redo cipher names chart (April King), move version chart (April King), update Intermediate cipher suite (ulfr) |
| 3.7 | Julien Vehent | cleanup version table (April King), add F5 conf samples (warburtron), add notes about DHE (rgacogne) |
| 3.6 | Julien Vehent | bump intermediate DHE to 2048, add note about java compatibility |
| 3.5 | alm | comment on weakdh vulnerability |
| 3.4 | Julien Vehent | added note about session resumption, HSTS, and HPKP |
| 3.3 | Julien Vehent | fix SHA256 prio, add POODLE details, update various templates |
| 3.2 | Julien Vehent | Added intermediate compatibility mode, renamed other modes |
| 3.1 | Julien Vehent | Added non-backward compatible ciphersuite |
| 3 | Julien Vehent | Remove RC4 for 3DES, fix ordering in openssl 0.9.8 (1024430), various minor updates |
| 2.5.1 | Julien Vehent | Revisit ELB capabilities |
| 2.5 | Julien Vehent | Update ZLB information for OCSP Stapling and ciphersuite |
| 2.4 | Julien Vehent | Moved a couple of aes128 above aes256 in the ciphersuite |
| 2.3 | Julien Vehent | Precisions on IE 7/8 AES support (thanks to Dobin Rutishauser) |
| 2.2 | Julien Vehent | Added IANA/OpenSSL/GnuTLS correspondence table and conversion tool |
| 2.1 | Julien Vehent | RC4 vs 3DES discussion. r=joes r=tinfoil |
| 2.0 | Julien Vehent, kang | Public release. |
| 1.5 | Julien Vehent, kang | added details for PFS DHE handshake, added nginx configuration details; added Apache recommended conf |
| 1.4 | Julien Vehent | revised ciphersuite. Prefer AES before RC4. Prefer 128 before 256. Prefer DHE before non-DHE. |
| 1.3 | Julien Vehent | added netscaler example conf |
| 1.2 | Julien Vehent | ciphersuite update, bump DHE-AESGCM above ECDH-RC4 |
| 1.1 | Julien Vehent, kang | integrated review comments from Infra; SPDY information |
| 1.0 | Julien Vehent | creation |
| Document Status: | READY | |