Badges/Onboarding-Issuer: Difference between revisions
Jadeforester (talk | contribs) |
Jadeforester (talk | contribs) |
||
| Line 1: | Line 1: | ||
== A. Mozilla Open Badge Infrastructure (OBI) == | == A. Mozilla Open Badge Infrastructure (OBI) == | ||
NOTE: The documentation below is for general on-boarding. If you want the more technical documentation, please see our [https://github.com/mozilla/openbadges/wiki/Issuer-API github pages]. | NOTE: The documentation below is for general on-boarding. If you want the more technical documentation, please see our [https://github.com/mozilla/openbadges/wiki/Issuer-API github pages]. | ||
=== I. BACKGROUND === | === I. BACKGROUND === | ||
Revision as of 15:10, 5 February 2014
A. Mozilla Open Badge Infrastructure (OBI)
NOTE: The documentation below is for general on-boarding. If you want the more technical documentation, please see our github pages.
I. BACKGROUND
Why Are We Doing This?
Learning happens everywhere. Yet it's often difficult to be recognized for skills and achievements that are gained outside of school. Mozilla's Open Badges project is working to solve that problem by making it easy for anyone anywhere to issue, earn, and display badges. The results: broad recognition of 21st century skills, unlocking of career and educational opportunities, and learners everywhere being able to level up in their lives and work.
Goals
- Develop badges as a system for alternative accreditation, credentialing, and recognition;
- Help badges expand beyond siloed environments to be broadly shareable;
- Truly support learners learning everywhere;
- Optimize the value of those badges by allowing badges to be remixable and shareable with different audiences;
- Develop a supporting infrastructure to standardize the process and support each learner;
- Create an infrastructure that is open and as decentralized as possible to give learners control and support of the entire ecosystem.
Description
Enabling learners to earn badges wherever they're learning across the web requires support for multiple individual badge issuers. Empowering learners to use their badges as legitimate credentials requires support for sharing of badges across many display sites. The Open Badges framework is designed to allow any learner to collect badges from multiple sites, tied to a single identity, and then share them out across various sites, including personal blogs to social networking channels. It is critical for this infrastructure to be open to give learners control over their own learning and credentials, allow anyone to issue badges, and for each learner to carry their badges with them across the Web and other contexts.
II. TECH SPECS
- The OBI is built in node.js using express.
- Badges are represented by JSON data blobs embedded in PNG files in the Backpack
- Identity management is handled by Mozilla’s Persona (fka BrowserID) [link: https://browserid.org/, http://identity.mozilla.com/]
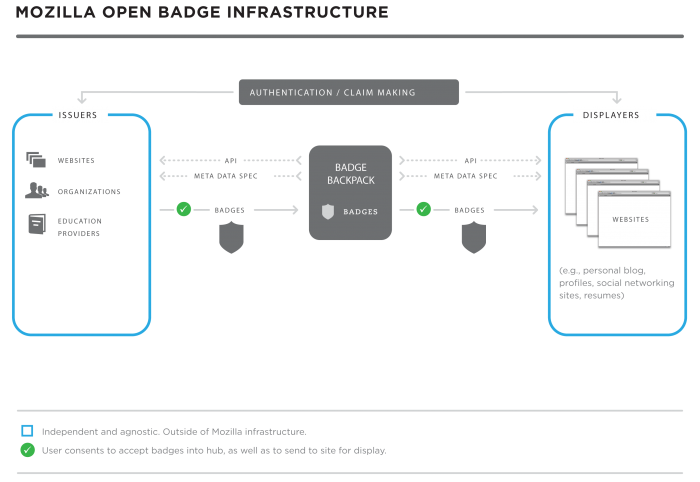
III. OPEN BADGES ECOSYSTEM
Diagram
Overview
- An issuing organization or individual makes a badge or series of badges available on their website and prompts their community to earn them. The earner sends the badge to their Backpack.
- The badge becomes portable through the Issuer API which provides script to present the earner with a modal dialog that requests their consent to add the issuer's badge(s) to their Backpack.
- Issuer can also push badges to the Mozilla Baking Service where the assertion URL representing JSON blobs is embedded into PNG files
- n.b. This is only necessary if the issuer wants the earner to have the ability to store badges outside of the OBI. Otherwise badge baking is handled through the Issuer API.
- Displayers pull unpacked badges (JSON) out of the Backpack based on earner action and privacy settings.
- Public badges are discoverable based on earner’s email address.
- Earners can share their badges through their Backpack and grant permission for a particular site to display that collection of badges.
- Displayers authenticate badges with the Issuer using the Verification check.
IV. DEFINITIONS/KEY TERMS
- Badge
The core currency of exchange. A single signal that demonstrates a skill, achievement, interest, or affiliation.
- Open Badge Infrastructure (OBI)
Open infrastructure technology supports independent badge issuers, display sites, and reference implementation of the badges Backpack. Includes the metadata spec, APIs, verification framework, and badges Backpack.
The core authorized data store and management interface of Mozilla’s reference implementation of the Backpack. Each earner has their own Backpack where their badges data is stored.
The definition of the information behind the badge. Each badge features a set of metadata that describes the badge, including badge name, badge issuer, date of issue, criteria URL, evidence URL, and standards URL.
Embedding the assertion URL (which points to all metadata) into a PNG file to create a fully robust, portable badge.
Interface specifications for sending badges to the Backpack.
The interface specifications for expanding badges beyond the Backpack (including display sites and widgets).
- Verification API
Communication channels and framework to support badge verification.
- Endorsement API
Communication channels and framework to support badge endorsement, including focuses on valid signatures.
- n.b. Endorsement employs the same signing mechanism as Badge Verification
- Badge Earner
A learner who stores their badges and engages with the Open Badges Infrastructure. This learner has had interactions with issuers to earn badges and uses their Backpack to manage and share those badges.
- Issuer
Organization or individual who issues Open Badges to their communities.
- Displayer
A website, organization, or person who accesses publicly shared Open Badges and displays them for badge earners.
- Endorser
An organization or individual who “endorses” a badge by signing it with their private encryption key. Trusted third party signers may emerge.
B. Issuer
An organization or individual who issues designs and issues badges into the ecosystem. The OBI is open and supports any independent issuer who conforms to the necessary badge and issuing specifications.
I. BACKGROUND
- Issuers completely determine the content and criteria behind their badge systems. They know their communities best.
- The touchpoint with the OBI occurs when earners send their badges to the designated Backpack.
- Issuers do not need to register with the OBI; they simply send badges to earner's Backpacks utilizing the Issuer Javascript API.
II. REQUIREMENTS
- Issuers must have web server capable of serving requests to the general Internet.
- Issuers must have hosting ability.
- Issuers must have ability to make a POST request from their server backend and read a JSON response.
- Issuers must have email addresses for earners and must be able to email earners.
- Issuers must have badges (or be able to convert their badges) into the format (metadata spec) that the Assertion expects.
- Earners must be registered with the backpack implementation that the issuer is trying to send their badges to. In the future, the issuer will need to ask the earner which backpack they want to push badges their to and honor that request.
- For verification:
- If doing Hosted Assertions (currently available).
- Issuers must maintain a server with the Badge Assertion information (at the unique badge URL) to verify each badge.
- If doing Signed Assertions.
- Issuers must generate public/private key pair and maintain the hosted public key.
- Issuers must sign the badges themselves, sign the whole package, and push badges to earner backpacks through the Issuer Javascript API.
- If doing Hosted Assertions (currently available).
III. BADGE CREATION FLOW
- Have an email address for the earner.
- Create and host an Assertion on site.
- Create and host the badge PNG; this is a single PNG for all badges, not a single physical PNG per issued badge.
- Integrate your site with the Backpack via the Issuer API
The Issuer API is a script that can be dropped into any badge issuer's website to provide a way for earners to add an issuer's badges to their Backpack or federated backpacks. There's no need to bake the badges independently as the API takes care of this.
IV. OPEN BADGES Related Widgets created by the community
- https://github.com/lmorchard/django-badger -- Issuing app for Django
- https://github.com/PRX/badges_engine -- Rails Engine for issuing.
- https://github.com/openmichigan/open_badges -- Drupal module for managing/issuing badges
n.b. Updated list can be found here: https://github.com/mozilla/openbadges/wiki/Open-Badges-related-widgets
V. Open Badger
OpenBadger will be a lightweight OBI compliant badge issuing platform. It will soon make creating and issuing badges easy for non-technical users. We've done some speculation but more to come on the Open Badger github.
C. Badge
- Representation - Assertion URL representing chunks of JSON data embedded into a PNG file.
- Badge Assertion aka Badge Manifest - Earner identity information (<algorithm>$<hash(email + salt)>) plus badge information (JSON metadata).
- Verified Badge - Badges that have an Assertion URL. The OBI currently supports verification of badges through Hosted Assertions. When the issuer sends a badge, metadata is pushed to a unique and persistent URL (the assertion URL). The issuer maintains badge Assertion and displayers can ping the assertion URL to confirm verification.
- Endorsed Badge - Badges that have been signed by a third party or endorser. The Backpack verifies the signature against the signer’s public key, and if confirmed, accepts the badge as an endorsed badge. The endorsement information is represented with the badge as a layer of trust on the badge’s validity.
- n.b. On development roadmap for 2013.
D. Backpack
The Mozilla Backpack is an authorized data storage space and management interface for earners of Open Badges. Each earner can access their own Backpack that holds all of their badges and gives them an interface to manage and share their badges.
- The Backpack is open source and federated. Earners or issuers can take the code and fork it.
- Earners may decide to create and host their own Backpack so that they have complete control over their badges.
- Mozilla has built a reference or default Backpack (the "Mozilla Backpack") which holds all of the badge Assertions (hashed user email + badge data) for each earner.
E. Metadata Spec
I. OVERVIEW
- A badge is an assertion URL representing chunks of JSON data embedded into a PNG file.
- The metadata should carry all the information needed to understand a badge. This ensures that badges can be fully understood and verified no matter where they are shared.
- This is the data presented in the Assertion URL on the issuer's server.
II. FIELDS
- Required
- recipient: Salted hash of the email address for the earner receiving the badge.
- salt: The salt used in the hash construction of the recipient’s email address.
- badge: The structure describing the badge.
- version: The version of the badge
- name: Human-readable name of the badge being issued. Maximum of 128 characters.
- image: URL for image representing the badge. Should be a square and in PNG format. Maximum size is 256kb.
- description: Description of the badge being issued. Maximum of 128 characters.
- criteria: URL describing the badge and criteria for earning the badge (not the specific instance of the badge).
- issuer: Information about the issuer:
- origin: Origin of the issuer. This is the <protocol>://<host>:<port>. Must match the origin of the Hosted Assertion (and in the future, the origin of the public key).
- name : Human-readable name of the issuing agent.
- Optional
- evidence: Earner-specific URL with information about this specific badge instance. Should contain information about how the individual earner earned the badge.
- expires: Date when the badge expires. If omitted, the badge never expires.
- standard: Information about a governing institution or standard that a badge is related to.
- The badge is not removed from the earner’s Backpack after the expiration date; there will be some visual/technical indicator that the badge is expired and needs to be re-upped. Must be formatted "YYYY-MM-DD" or a unix timestamp.
- issued_on: Date when badge was issued. If omitted, the issue date will be set to the date the badge was pushed to the Backpack. Must be formatted "YYYY-MM-DD" or a unix timestamp.
- issuer: Information about the Issuer:
- org: (OPTIONAL) Organization for which the badge is being issued. An example is if a scout badge is being issued, the "name" of the Issuer could be "Boy Scouts" and the "org" could be "Troop #218".
- contact: (OPTIONAL) A human-monitored email address associated with the Issuer.
Issuers can put a reasonable amount of extra material into the badge, but that material must be static -- once the badge is issued, any change to that information must not change. This is to prevent someone from issuing one badge, then sneakily changing it later to another badge unbeknownst to the earner.
F. PNG Files / Badge Baking Service
I. BACKGROUND
- Each badge is a JSON blob of metadata embedded in a PNG file.
- This allows the badge to be more easily portable - an actual collection of information that can be emailed around and portable while still carrying its details with it.
- Ultimately, this is important for decentralization of the system and will allow earners to have more control over where their badges live.
II. BETA: BAKING SERVICE
- REQUIREMENTS: To bake a badge, you must be hosting a badge Assertion on your site.
- See the Assertions page for details: https://github.com/mozilla/openbadges/wiki/Assertions
- Issuers will still send the badge Assertion to Mozilla, but instead of sending it directly to the Backpack, they will now send it to the Mozilla Baking Service. Then Mozilla will package it into a PNG and deliver back to the issuer who can then send to the earner.
- The purpose of this is:
- A) to avoid SPAMing the Earner with unwanted badges, and
- B) to give the Earners ultimate control over where the badges go.
- n.b. If you are building a new system, we strongly recommend using the Javascript Issuer API for awarding badges. The API takes care of the badge baking for the Issuer.
- The purpose of this is:
- Mozilla provides the "tools" for unpacking the PNG file through the OBI.
- PNG files will be unpacked in the Backpack where each earner can view, manage, and organize their badges (and see all the metadata behind each badge).
- PNG files will be unpacked for the Displayer API so that Displayers will just have the raw data to work with on their end.
III. BADGE IMAGE STANDARDS
- Image must be a PNG.
- Images should be square and not exceed 256kb. They should have dimensions not smaller that 90 x 90.
- Image is provided as a URL to the image on the issuer server in the metadata.
- Mozilla will cache the image in at least two sizes.
- When a badge is displayed, it will be loaded from the Mozilla cache to avoid extra burden on the issuer servers. This also helps if the issuer is not available or the link is broken.
G. Verification
I. OVERVIEW
- To avoid gaming and duplication, the OBI is built to support badge verification.
- This helps handle the questions of "Did this Issuer issue this badge to this earner on this date? Is this badge still valid or has it expired?"
- The OBI provides the channel for this verification to happen through the Backpack but must communicate with the Issuer.
- The issuer must be online to verify badges. (We are exploring a cache to cover verification for a set amount of time).
- Most verification will be done by displayers. Displayers should not display a badge that cannot be verified.
II. VERIFICATION METHOD
- The OBI currently supports verification of badges through Hosted Assertions. When an issuer sends a badge using the OBI, metadata is pushed to a unique and persistent URL (the Assertion URL). The issuer maintains the badge Assertion and displayers can ping the assertion URL to verify the badge.
- A displayer puts the earner’s email address through a salted hash function and sees if it matches with the hash value indicated for the recipient in the badge metadata. If values match, the badge belongs to the earner and can be claimed.
- There is a drawback of overhead for the issuer to maintain unique and persistent URLs for each badge.
- With the V1.0 release we support Signed Assertions, allowing for signing of a badge assertion with a private key and hosting a public key at a public URL.
- This has the benefit of creating less overhead for the issuer who just need to host the public key.
- Looking forward, we will try to support DNSSEC for public key discovery.
- Unverified Badge handling
- If a badge is passed through by an issuer and the signature is invalid, it is rejected.
- If a badge is verified initially but it becomes unverified in the future, the earner is notified.
III. FUNCTIONAL FLOW
- Badge (within it, its assertion) exists in the Backpack.
- User attempts to display badge via a display site widget.
- Display site takes the earner’s email and puts it through a salted hash function.
- eg. hash (‘hipjoe@example.com’ + salt)
- Display site compares the resulting value with the value indicated for the recipient in the badge metadata.
- If values match, badge is verified and displayer displays the badge. If not, displayer should reject the badge.
H. Displayers
- Display of badges is where a significant part of the value of this approach lies. Badges are not siloed or limited to one site but can be combined with badges from multiple issuers and then shared for different audiences and purposes.
- Each earner will control where badges are displayed through the Backpack.
- Each earner can create collections of badges and share with displayers that have connected to the Displayer API.
- Earners can also make badges public; those badges would be discoverable by displayers if they had the earner’s email address.
- If a site has an earner's email address, they will be able to query that person's Backpack for all of that earner's public badges. They will get back JSON representation of the badges.
I. Identity
I. OVERVIEW
- Identity is a critical component because we need to recognize earners as they earn badges from different issuers.
- It's important to us that identity be open and decentralized.
- We are utilizing verified email as a form of identity through the Mozilla product Persona.
- Additional info: https://browserid.org/, https://wiki.mozilla.org/Identity
- Many sites already use email addresses for logins, even those that don't generally collect them.
- We don't need to retain any profile or personal information about the earner; all we need is their email address.
II. FUNCTIONAL FLOW FOR VERIFYING IDENTITY IN BACKPACK
- User validates identity to Mozilla's Verified Email.
- User creates an account with Mozilla (same as sync account).
- User asserts which email addresses he or she owns.
- User does an SMTP challenge (system emails user a token link they must click) to prove ownership.