Security/Foreign Certificate Warning
< Security
Jump to navigation
Jump to search
Description
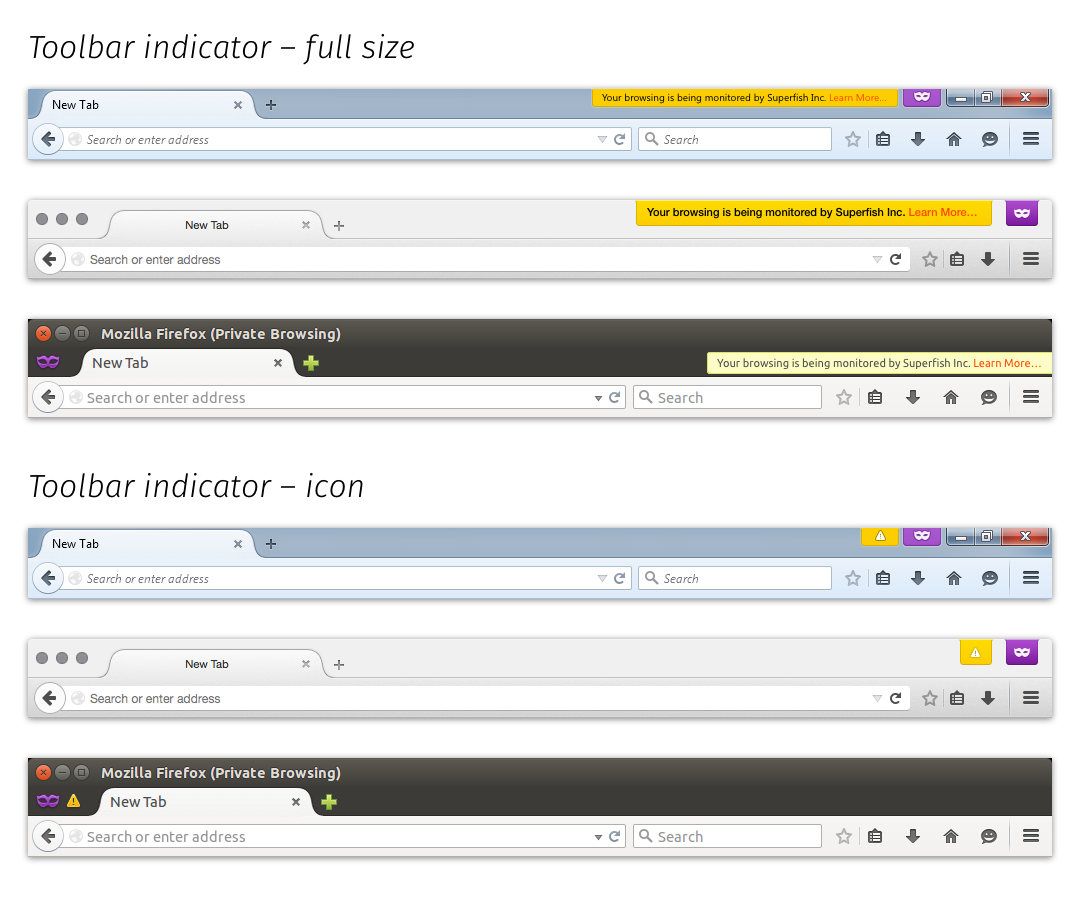
Firefox shows a non-dismissable banner at the top of each page when the site you're connecting to uses a dodgy cert somewhere down in the chain.
The precise definition of a dodgy cert is TBD but it would trigger when a root cert is added that's not part of the Mozilla CA program and is part of the chain for the currently visited site.
Requirements
- Security Engineering:
- Persistent, non-dismissable message in a fairly prominent place
- Looks like a warning (or a reminder), not an error message
- User Experience:
- Consumes zero site real estate
- Message can resize to consume minimal tab real estate (it still has to consume some space, but we minimised it as much as we could)
- Not in-your-face; users won’t get annoyed and switch browsers
Use cases
- Malware: a user bought a new Lenovo laptop and has the Superfish root cert installed in their browser.
- User action: take steps to remove the malware and then verify that the warning is gone
- Corporate surveillance: a user works in a company that deals with sensitive data and monitors all employee web browsing as per their employment contract
- User action: avoid visiting personal sites on company property
- User action: if the website (e.g. online banking) should be whitelisted and not mitm'ed, contact local system administrator to get this fixed
- Parental filter: a parent installs a surveillance proxy to watch what their children are doing online
- User action: none, but keep in mind that your parents are watching
- Anti-virus products: a user installs an anti-virus product which scans all visited sites for malware
- User action: none, your traffic are protected by the XYZ Security Suite
- Debugging: a developer installs mitmproxy to debug TLS traffic
- User action: don't forget to remove the mitmproxy root cert once you're done testing
Impact
The banner is a warning, not an error. There are lots of legitimate reasons why a non-Mozilla approved root cert can be added to the browser.
However, in almost all of these legitimate cases, the extra warning can be said to be a useful reminder.
In the non-legitimate use cases, the warning can alert users to a serious security problem.
Challenges
- By showing a warning, you can perceive that Firefox is broken and switch to another browser that doesn’t show any warnings.
- Clicking on the warning should open a page in content (similar to what we do for invalid HTTPS certs) which explains the possible causes of this warning and what you can do about it.
- Whatever happens, we must assure user that Firefox is not broken. On the contrary, it’s the other browsers that aren’t showing them any warnings. It's an opportunity to show the user that we care and that we have their back.
- Often, nothing you do will fix the problem because the root cert reinstalls itself and the problem is deeper (e.g. Superfish)
- We should steer people towards the SUMO page on how to remove malware.
- The name of the certificate issuer is under the controller of the person minting the cert (i.e. the attacker in malicious cases).
- Organizations using private CAs would be affected by this even though in this case there is no MITM (see rsleevi's comment on a similar feature).
- It's not clear whether this would be perceived as bad for internal sites (see mnot's comment).
- Giving users a simple explanation for why this is something they should worry about and giving them some actionable suggestions for resolution/mitigation.
Related
- Bug 1135776: show a different UI for certificates issued by non-built-in root certificates
- Chromium bug 81623 (equivalent Chromium bug)